Let us know how we can help
Sales & Pricing
Speak to a rep about your business needs
Help & Support
See our product support options
General inquiries and locations
Contact usWhat is DORA? The Digital Operational Resilience Act Explained
DORA is a regulation that enhances the operational resilience of information and communication technology (ICT) and third-party providers in the EU financial sector.
The Digital Operational Resilience Act, also known as DORA, is a pivotal EU regulation designed to enhance the operational resilience of digital systems that support financial institutions operating in European markets, with a comprehensive focus on risk management, incident response, and governance.

Featured learning experience:
The Digital Operational Resilience Act (DORA) and Your Mainframe System (2:02)
watch nowDORA regulations fortify mainframe operations and ensure resilience to shield your organization from financial penalties and reputational risks.
Jason Bloomberg
Intellyx | Founder & Principal Analyst
Provided for informational purposes only. This information should not be considered legal advice, and may not reflect the latest in legal/regulatory/compliance/etc. Always consult with council or qualified legal professionals, and/or relevant authorities.
What you need to know about DORA
- The Digital Operational Resilience Act timeline started with formal adoption by the Council of the European Union and the European Parliament in November 2022, and DORA regulations will go into effect on January 17, 2025.
- Financial entities and third-party ICT service providers have until January 17, 2025, to comply with DORA before enforcement starts.
- The DORA law addresses key components such as service visibility, risk mitigation, business continuity, incident management, and governance, guiding organizations in building resilient frameworks that withstand challenges and align with the dynamic landscape of digital operations.
The purpose of DORA
Why is DORA happening?
- There is currently no framework for the management and mitigation of ICT risk that spans the entire European financial sector.
- The DORA regulatory act aspires to establish a framework by comprehensively harmonizing risk management rules across the EU and ensuring that every financial institution is held to the same high standard.
- DORA compliance aims to eliminate the complexities arising from gaps, overlaps, and conflicts between diverse regulations in different member states, streamlining compliance for financial entities while enhancing the resilience of the entire EU financial system.
What are the 5 pillars of DORA?
The 5 pillars of DORA are:
ICT risk management and governance
This requirement involves strategizing, assessing, and implementing controls. Accountability spans all levels, with entities expected to prepare for disruptions. Plans include data recovery, communication strategies, and measures for various cyber risk scenarios.
Incident reporting
Entities must establish systems for monitoring, managing, and reporting ICT incidents. Depending on severity, reports to regulators and affected parties may be necessary, including initial, progress, and root cause analyses.
Digital operational resilience testing
Entities must regularly test their ICT systems to assess protections and identify vulnerabilities. Results are reported to competent authorities, with basic tests annually and threat-led penetration testing (TLPT) every three years.
Third-party risk management
Financial firms must actively manage ICT third-party risk, negotiating exit strategies, audits, and performance targets. Compliance is enforced by competent authorities, with proposals for standardized contractual clauses under exploration.
Information sharing
Financial entities are urged by the DORA to develop incident learning processes, including participation in voluntary threat intelligence sharing. Shared information must comply with relevant guidelines, safeguarding personally identifiable information (PII) under the EU's General Data Protection Regulation (GDPR).
Focus areas of DORA for the mainframe
The Digital Operational Resilience Act’s core principles ensure that financial institutions understand their entire IT landscape, including their third-party service suppliers, and can identify potential vulnerabilities and risks and implement robust automated strategies to protect their systems, data, and customers from cyberthreats and other disruptions. While the DORA regulatory focus is on ICT and third-party risk management, incident reporting, resilience testing, and information sharing, firms with mainframe systems should also consider the following:
Service awareness and availability
Implement regular health checks, automated maintenance tasks, and predictive alarms based on workload patterns.
- Enhance visibility through logging mechanisms aligned with DORA's transparency requirements that provide real-time insights into mainframe activities.
- Ensure a proactive approach to potential issues and promote transparency and accountability in line with DORA regulations.
Risk management
Conduct regular vulnerability assessments, security control enhancements, real-time monitoring, and penetration testing to identify and remediate vulnerabilities unique to the mainframe architecture.
- Stay informed and updated about security patches and updates relevant to mainframe systems.
- Evaluate and update security and enhance access controls, encryption mechanisms, and authentication processes to enable DORA compliance.
- Detect and respond promptly to security threats and integrate threat intelligence feeds to stay informed about emerging mainframe-specific threats.
- Address exposures and vulnerabilities in hardware, system, and security configurations by conducting regular reviews, updates, and security audits.
Business continuity management
Develop robust recovery plans and automated backup solutions that include detailed procedures for various failure scenarios.
- Ensure a plan’s testability by conducting simulation exercises and audits to ensure its effectiveness in real-world scenarios.
- Incorporate failover mechanisms to secondary mainframe systems for continuous operations in the face of unexpected failures.
- Automate backup solutions for mainframe data and ensure regular and consistent backups are key components, with an emphasis on testing and validating backup and recovery procedures.
- Introduce immutable copies of critical data to enhance data resilience and establish safeguards against malicious activities and cyberthreats.
- Address ransomware with preventive measures for detecting, isolating, and recovering from ransomware attacks.
- Migrate mainframe backup data and tape data to cloud storage options for improved scalability, availability, and disaster recovery.
- Leverage cloud capabilities to ensure the ability to recover mainframe data anywhere and enhance the recovery time objective (RTO) and recovery point objective (RPO).
Incident management
Seamlessly integrate mainframe monitoring alerts into the overall enterprise service console to provide a unified view of incidents and effectively manage them across the organization.
- Establish integration and cohesive coordination between the mainframe and the Security Operations Center (SOC), transmitting critical security events in real time for immediate analysis and response.
- Develop automated response playbooks for common threat scenarios on the mainframe, incorporating actions such as isolating affected systems or blocking malicious activity.
- Continuously refine and update automated response mechanisms based on evolving threats to ensure a dynamic and effective incident management approach aligned with DORA standards.
Governance and compliance
Enforce compliance with vulnerability evaluations, compliance checks, and continuous adherence to regulatory standards to safeguard mainframe systems from potential fines and reputational risks.
- Leverage vulnerability scanning tools specific to the mainframe environment that implement automated processes for identifying and prioritizing vulnerabilities.
- Integrate vulnerability assessment results into governance and compliance reporting to streamline processes and ensure adherence to DORA requirements.
- Establish automated compliance checks for mainframe policies, industry regulations, and certificates, with regular audits and validations of compliance requirements.
- Remediate non-compliance issues quickly with automated, recurring, and scheduled reporting that provides timely updates.
- Design governance processes that evolve continuously to align with DORA, ensuring a proactive and adaptive approach to mainframe governance.
Service awareness and availability
Implement regular health checks, automated maintenance tasks, and predictive alarms based on workload patterns.
- Enhance visibility through logging mechanisms aligned with DORA's transparency requirements that provide real-time insights into mainframe activities.
- Ensure a proactive approach to potential issues and promote transparency and accountability in line with DORA regulations.
Risk management
Conduct regular vulnerability assessments, security control enhancements, real-time monitoring, and penetration testing to identify and remediate vulnerabilities unique to the mainframe architecture.
- Stay informed and updated about security patches and updates relevant to mainframe systems.
- Evaluate and update security and enhance access controls, encryption mechanisms, and authentication processes to enable DORA compliance.
- Detect and respond promptly to security threats and integrate threat intelligence feeds to stay informed about emerging mainframe-specific threats.
- Address exposures and vulnerabilities in hardware, system, and security configurations by conducting regular reviews, updates, and security audits.
Business continuity management
Develop robust recovery plans and automated backup solutions that include detailed procedures for various failure scenarios.
- Ensure a plan’s testability by conducting simulation exercises and audits to ensure its effectiveness in real-world scenarios.
- Incorporate failover mechanisms to secondary mainframe systems for continuous operations in the face of unexpected failures.
- Automate backup solutions for mainframe data and ensure regular and consistent backups are key components, with an emphasis on testing and validating backup and recovery procedures.
- Introduce immutable copies of critical data to enhance data resilience and establish safeguards against malicious activities and cyberthreats.
- Address ransomware with preventive measures for detecting, isolating, and recovering from ransomware attacks.
- Migrate mainframe backup data and tape data to cloud storage options for improved scalability, availability, and disaster recovery.
- Leverage cloud capabilities to ensure the ability to recover mainframe data anywhere and enhance the recovery time objective (RTO) and recovery point objective (RPO).
Incident management
Seamlessly integrate mainframe monitoring alerts into the overall enterprise service console to provide a unified view of incidents and effectively manage them across the organization.
- Establish integration and cohesive coordination between the mainframe and the Security Operations Center (SOC), transmitting critical security events in real time for immediate analysis and response.
- Develop automated response playbooks for common threat scenarios on the mainframe, incorporating actions such as isolating affected systems or blocking malicious activity.
- Continuously refine and update automated response mechanisms based on evolving threats to ensure a dynamic and effective incident management approach aligned with DORA standards.
Governance and compliance
Enforce compliance with vulnerability evaluations, compliance checks, and continuous adherence to regulatory standards to safeguard mainframe systems from potential fines and reputational risks.
- Leverage vulnerability scanning tools specific to the mainframe environment that implement automated processes for identifying and prioritizing vulnerabilities.
- Integrate vulnerability assessment results into governance and compliance reporting to streamline processes and ensure adherence to DORA requirements.
- Establish automated compliance checks for mainframe policies, industry regulations, and certificates, with regular audits and validations of compliance requirements.
- Remediate non-compliance issues quickly with automated, recurring, and scheduled reporting that provides timely updates.
- Design governance processes that evolve continuously to align with DORA, ensuring a proactive and adaptive approach to mainframe governance.
DORA operational resilience toolchain
DORA outlines five considerations for rapid response, recovery, and compliance that align with the aforementioned key aspects of DORA as they relate to the mainframe.
Identify
Understanding risk to systems, people, assets, data, and capabilities, including business context, policies, and vulnerabilities.
Protect
Ensure safeguards to limit or contain the impact of a potential cybersecurity event. Fortify defenses to ensure the integrity and security of critical data and systems.
Detect
Discover cybersecurity events and anomalies in real time and understand their potential impact. Identify and understand potential threats for swift mitigation.
Respond
Take action to limit the impact of cybersecurity events and anomalies. Well-defined response mechanisms and protocols in place.
Recover
Restore data, systems, and operations to normal conditions. Ensure systems can bounce back efficiently and effectively.
BMC solutions for DORA focus areas
BMC offers a range of solutions that address the full scope of the five focus areas outlined above, as well as specific sub-focus areas within each, as follows.
Service awareness and availability
Proactive mainframe monitoring and automation
Identify and control problems quickly with a single view and unite AIOps processes across the business with data sharing.
Improve productivity, increase system availability, manage alarms and events generated by monitor components, and automate mainframe event data integration for your operations management systems.
AI predictive mainframe monitoring
Detect problems and generate notifications before they impact the business with an AI solution that conducts multivariate analysis for all KPIs simultaneously and is continuously learning.
Risk management
Mainframe threat detection and automated response
BMC AMI Command Center for Security and BMC AMI Datastream
Reduce risk, strengthen your security posture, and stop threats before the threaten your environment with configurations and recommendations designed by mainframe hacking experts.
BMC AMI Security Session Monitor
Deter insider threats by capturing and analyzing start-to-finish user session activity that provides deep insight into user behaviors; identify and reduce cybersecurity threats with unique methodologies.
BMC AMI Enterprise Connector for Illumio
Identify and control network traffic by automatically converting Illumio micro segmentation rules into TCP/IP mainframe rules to increase productivity and security.
Mainframe penetration testing and security assessment (baselining)
BMC Mainframe Services: Penetration Testing
Get regular and ongoing professional checkups that include security evaluations via a simulated “real-world” attack from an experienced BMC pentesting team.
BMC Mainframe Services: Mainframe SWIFT Assessment Service
Reduce the risk of internal and external attacks with a review by BMC specialists who can reveal weaknesses and vulnerabilities so you can plug gaps in your defenses and secure your mainframe.
Business continuity management
Database recovery
Assure your required resources are available for recovery by estimating and simulating recovery scenarios and automating, accelerating, and streamlining backup and recovery jobs.
Check the data integrity of all unstructured or line of business (LOB) objects and data and fix any correctable errors.
BMC AMI Backup and Recovery for IMS™
Estimate, simulate, and educate your team about recovery scenarios to ensure compliance and meet your recovery time objectives (RTOs) with point in time (PIT) recovery capabilities.
Ransomware recovery
BMC AMI Command Center for Security
Leverage this integrated solution set to identify the time of an attack, identify the golden copy back up, and restore the database after the last clean backup to with minimal data loss. Recover anywhere even if the primary site was compromised.
Cloud backup management
Use object storage data protection capabilities like immutable copies and back up a third, or “golden” copy to, and recover directly from, the cloud with no dependency on a compromised system.
Simulate business capacity scenarios
BMC Helix Continuous Optimization for Mainframes and BMC AMI Capacity Management
Proactively diagnose and prevent capacity-driven performance problems, validate system investments, right-size your environment, and reduce costs with accurate, comprehensive performance monitoring.
Database resilience
BMC AMI Database Integrity for IMS™
Protect the integrity of your IMS data by addressing the most common cause of IMS database problems, cross-referencing control block libraries, and auditing database definition (DBD) libraries.
Transaction resilience and recovery
BMC AMI Message Advisor for IMS™
Automatically monitor and manage IMS message queues to reduce restart times, prevent IMS outages, and improve IMS availability.
Incident management
Proactive mainframe monitoring and automated threat response
BMC AMI Command Center Security
Prevent and mitigate cyberattacks with AI-enabled, real-time behavioral analytics that identify known indicators of compromise (IOCs) and automated responses. Pinpoint the source and time of attacks, enabling identification of the golden copy from which to recover.
Proactive mainframe monitoring and automation
Automate event integration and send mainframe event data to BMC Helix Operations Management or other enterprise-wide operations management systems.
Governance and compliance
Mainframe security policy compliance
BMC AMI Security Policy Manager
Harden the mainframe from attacks and quickly uncover and address security gaps before a compromise or exploit can occur with automatic configuration scanning, recommendations, and reporting.
BMC AMI Command Center Security
Recognize suspicious user behavior and identify possible cyberattacks and ransomware threats in real time with AI-enabled tools.
Simplify the complex task of preparing data for testing without writing programs or scripts and without leaving the streamlined interface. Ensure data integrity based on referential integrity or application relationships, and mask sensitive test data.
Mainframe certificate management
BMC AMI Enterprise Connector for Venafi
Improve quality and reduce time and manual certificate management with an automated approach that can implement and deploy hundreds to thousands of certificates every month.
Service awareness and availability
Proactive mainframe monitoring and automation
Identify and control problems quickly with a single view and unite AIOps processes across the business with data sharing.
Improve productivity, increase system availability, manage alarms and events generated by monitor components, and automate mainframe event data integration for your operations management systems.
AI predictive mainframe monitoring
Detect problems and generate notifications before they impact the business with an AI solution that conducts multivariate analysis for all KPIs simultaneously and is continuously learning.
Risk management
Mainframe threat detection and automated response
BMC AMI Command Center for Security and BMC AMI Datastream
Reduce risk, strengthen your security posture, and stop threats before the threaten your environment with configurations and recommendations designed by mainframe hacking experts.
BMC AMI Security Session Monitor
Deter insider threats by capturing and analyzing start-to-finish user session activity that provides deep insight into user behaviors; identify and reduce cybersecurity threats with unique methodologies.
BMC AMI Enterprise Connector for Illumio
Identify and control network traffic by automatically converting Illumio micro segmentation rules into TCP/IP mainframe rules to increase productivity and security.
Mainframe penetration testing and security assessment (baselining)
BMC Mainframe Services: Penetration Testing
Get regular and ongoing professional checkups that include security evaluations via a simulated “real-world” attack from an experienced BMC pentesting team.
BMC Mainframe Services: Mainframe SWIFT Assessment Service
Reduce the risk of internal and external attacks with a review by BMC specialists who can reveal weaknesses and vulnerabilities so you can plug gaps in your defenses and secure your mainframe.
Business continuity management
Database recovery
Assure your required resources are available for recovery by estimating and simulating recovery scenarios and automating, accelerating, and streamlining backup and recovery jobs.
Check the data integrity of all unstructured or line of business (LOB) objects and data and fix any correctable errors.
BMC AMI Backup and Recovery for IMS™
Estimate, simulate, and educate your team about recovery scenarios to ensure compliance and meet your recovery time objectives (RTOs) with point in time (PIT) recovery capabilities.
Ransomware recovery
BMC AMI Command Center for Security
Leverage this integrated solution set to identify the time of an attack, identify the golden copy back up, and restore the database after the last clean backup to with minimal data loss. Recover anywhere even if the primary site was compromised.
Cloud backup management
Use object storage data protection capabilities like immutable copies and back up a third, or “golden” copy to, and recover directly from, the cloud with no dependency on a compromised system.
Simulate business capacity scenarios
BMC Helix Continuous Optimization for Mainframes and BMC AMI Capacity Management
Proactively diagnose and prevent capacity-driven performance problems, validate system investments, right-size your environment, and reduce costs with accurate, comprehensive performance monitoring.
Database resilience
BMC AMI Database Integrity for IMS™
Protect the integrity of your IMS data by addressing the most common cause of IMS database problems, cross-referencing control block libraries, and auditing database definition (DBD) libraries.
Transaction resilience and recovery
BMC AMI Message Advisor for IMS™
Automatically monitor and manage IMS message queues to reduce restart times, prevent IMS outages, and improve IMS availability.
Incident management
Proactive mainframe monitoring and automated threat response
BMC AMI Command Center Security
Prevent and mitigate cyberattacks with AI-enabled, real-time behavioral analytics that identify known indicators of compromise (IOCs) and automated responses. Pinpoint the source and time of attacks, enabling identification of the golden copy from which to recover.
Proactive mainframe monitoring and automation
Automate event integration and send mainframe event data to BMC Helix Operations Management or other enterprise-wide operations management systems.
Governance and compliance
Mainframe security policy compliance
BMC AMI Security Policy Manager
Harden the mainframe from attacks and quickly uncover and address security gaps before a compromise or exploit can occur with automatic configuration scanning, recommendations, and reporting.
BMC AMI Command Center Security
Recognize suspicious user behavior and identify possible cyberattacks and ransomware threats in real time with AI-enabled tools.
Simplify the complex task of preparing data for testing without writing programs or scripts and without leaving the streamlined interface. Ensure data integrity based on referential integrity or application relationships, and mask sensitive test data.
Mainframe certificate management
BMC AMI Enterprise Connector for Venafi
Improve quality and reduce time and manual certificate management with an automated approach that can implement and deploy hundreds to thousands of certificates every month.
DORA regulation overview: Understanding the Digital Operational Resilience Act
First, a quick DORA (Digital Operational Resilience Act) summary. DORA is a comprehensive European union (EU) regulation designed to:
- Enhance and fortify operational resilience
- Establish unified incident response protocols
- Provide guidance for risk management and mitigation
- Shield organizations from information and communication technology (ICT)-related incidents, penalties, and reputational risk
The DORA regulatory legislation defines technical standards, capabilities, and outcomes to ensure all organizations under its jurisdiction follow a unified set of practices to maintain their security and continuous operations during incidents that threaten their ICT systems.
DORA and the financial sector
The DORA regulation applies to financial entities within the EU and the critical third-party ICT providers that serve them. These financial entities have undergone rapid digitalization. They are common targets for cyberattacks, and the fallout from suffering an incident impacts every other organization that depends on the financial entity’s core services.
Authorities within the EU drafted DORA to help financial organizations and their providers understand and manage risks, and ensure their services are operational at all times.
Timelines and milestones: DORA’s implementation schedule
DORA historical timeline
The following Digital Operational Resilience Act timeline summarizes the key moments in this legislation’s history.
DORA 2020
- September 24, 2020: EU commission publishes first draft
DORA 2021–2022
- 2021–2022: Co-legislators discussed legislation
DORA 2022
- November 10, 2022: Formally approved by the EU
- December 27, 2022: Published in the Official Journal
DORA 2023
- January 16, 2023: Entered into force
DORA 2024
- January 17, 2024: European Supervisory Authorities (ESAs) publish first set of rules for DORA
- March 12, 2024: ESAs publish joint feedback on second set of policies
DORA 2025
Key dates for DORA’s rollout
DORA goes into effect on January 17, 2025. On that date, all entities and providers under its purview must be in full compliance with its requirements, or they will be at risk for fines and penalties.
DORA 2020
- September 24, 2020: EU commission publishes first draft
DORA 2021–2022
- 2021–2022: Co-legislators discussed legislation
DORA 2022
- November 10, 2022: Formally approved by the EU
- December 27, 2022: Published in the Official Journal
DORA 2023
- January 16, 2023: Entered into force
DORA 2024
- January 17, 2024: European Supervisory Authorities (ESAs) publish first set of rules for DORA
- March 12, 2024: ESAs publish joint feedback on second set of policies
DORA 2025
Key dates for DORA’s rollout
DORA goes into effect on January 17, 2025. On that date, all entities and providers under its purview must be in full compliance with its requirements, or they will be at risk for fines and penalties.
Key terms to know
CTPPS (Critical Third-Party Providers)
The DORA regulation sets requirements for both financial entities and the third-party ICT providers that serve them. However, DORA only applies to what it defines as “critical” providers, and the legislation often refers to them as critical third-party providers, or CTPPS.
The legislation is somewhat ambiguous about what is considered a “critical” provider, though it relates to how integrated and important a service is for a financial entity’s operations. These providers are directly impacted by DORA and its authorities.
NISD (Network and Information Security Directive)
The Network and Information Security Directive (NISD) is a broader directive to improve the security and resilience of organizations and infrastructure within the EU. NISD applies to operators of essential services and relevant digital service providers, and imposes similar requirements to DORA.
NISD goes live in October 2024, a few months before DORA. Together, the two regulations make it clear that cybersecurity and resilience are core concerns for the EU, and additional legislation for other industries is likely to follow.
The three European Supervisory Authorities
DORA empowers multiple authorities to supervise its implementation, enforce its policies, and levy penalties for entities that fail to comply. These are often referred to as European Supervisory Authorities (ESAs), and they include:
ESMA (European Securities and Markets Authorities Providers)
An independent EU organization “whose purpose is to improve investor protection and promote stable, orderly financial markets.” (EU)
EIOPA (European Insurance and Occupational Pensions Authority)
A part of the European system of financial supervision that provides “advice to the European Commission, the European Parliament and the Council of the European Union.” (EU)
EBA (European Banking Authority)
An agency “tasked with implementing a standard set of rules to regulate and supervise banking across all EU countries.” (EU)
ESMA (European Securities and Markets Authorities Providers)
An independent EU organization “whose purpose is to improve investor protection and promote stable, orderly financial markets.” (EU)
EIOPA (European Insurance and Occupational Pensions Authority)
A part of the European system of financial supervision that provides “advice to the European Commission, the European Parliament and the Council of the European Union.” (EU)
EBA (European Banking Authority)
An agency “tasked with implementing a standard set of rules to regulate and supervise banking across all EU countries.” (EU)
The role of external oversight and the ESAs
The ESAs are the organizations that drafted DORA’s regulatory technical standards (RTS) and implementing technical standards (ITS). They are also responsible for assessing and enforcing compliance with the legislation.
Oversight as laid out in DORA
DORA authorities, including the ESAs, will evaluate compliance with the legislation’s requirements. They will perform direct oversight for both financial entities, and for third parties deemed critical ICT providers and under their jurisdiction.
These authorities will also collaborate with entities and providers, receive their reports of incidents and notifications of threats, and offer guidance and best practices for maintaining compliance.
Certain forms of oversight will be performed by entities and providers themselves. Entities are required to maintain oversight over their third-party ICT providers, and both groups are required to maintain awareness of their own risks.
How ESAs will enforce DORA
Entities and providers will be required to prove compliance with DORA’s requirements, which include vulnerability scans and assessments, annual recovery testing, physically and logically segregated data vaults, and rapid event reporting.
ESAs will also be empowered to perform audits, request information and documentation, and levy penalties. These can include financial penalties, denying approval for providers to work with DORA EU financial entities, and forcing an organization to cease to operations.
Who will DORA apply to?
Broadly speaking, the DORA regulation applies to financial entities operating within the EU and the third-party ICT providers that do business with them.
Identifying entities affected by DORA
DORA classifies 21 categories of financial activities that fall under its scope, which means the legislation applies to a wide range of financial entities and service providers. These include:
- Credit institutions
- Payment institutions
- Account information service providers
- Electronic money institutions
- Investment firms
- Crypto-asset service providers
- Central securities depositories
- Central counterparties
- Trading venues
- Trade repositories
- Managers of alternative investment funds
- Management companies
- Data reporting service providers
- Insurance and reinsurance undertakings
- Insurance intermediaries
- Institutions for occupational retirement provision
- Credit rating agencies
- Administrators of critical benchmarks
- Crowdfunding service providers
- Securitization repositories
- ICT third-party service providers
Understanding the implication for third-party providers
DORA sets requirements for “critical” third-party ICT providers that do business with financial institutions within the EU, even if those providers are not headquartered in the EU. DORA includes third-party ICT providers that appear location-agnostic, including cloud service providers, data center providers, and data analytics providers.
These new technical requirements will be written into contracts between financial entities and third-party ICT providers. At the moment, these contract requirements will be defined by the entities themselves, but it is possible that DORA will include standardized contracts or terms that must be used by providers and entities.
This would place third-party ICT providers under greater oversight and scrutiny from both the financial entities they support and EU financial authorities. Third-party ICT providers may also need to have a legal subsidiary within the EU to offer their services to financial entities within the EU.
DORA regulations broadly define which third-party ICT providers are deemed “critical” as any provider that offers important functions to financial entities, and whose services may impact a financial entity’s business stability and continuity.
Who is exempt from DORA?
DORA regulation offers limited exemptions for smaller financial entities that employ less than 10 people and have annual turnover and/or balance sheet totals under two million Euros. It also does not apply to certain entities exempt from related legislation. For them, DORA requires a simplified version of its ICT risk management framework.
In terms of third-party ICT providers, DORA sets requirements for providers deemed “critical,” as outlined above. However this remains a broad term, and it is unclear whether DORA will effectively apply to all providers that service financial entities.
Overall, DORA requirements follow the principle of proportionality. They are designed for financial entities that align with a specific size, risk profile, nature, scope, and complexity of services, activities, and operations. Under DORA, financial entities that meet these criteria will need to meet all of the act’s requirements.
The repercussions of non-compliance: Understanding the penalties
DORA outlines a range of specific fines and penalties for non-compliance. It also gives authorities the power to apply additional penalties at their discretion.
Penalties and fines for DORA non-compliance
Under DORA, financial entities that violate the act can be fined a periodic penalty of up to one percent of their average daily global turnover for up to six months (or until they achieve compliance). They may also be fined up to two percent of the annual global turnover. Third-party ICT providers are subject to the same potential penalties and fines.
Individuals who violate DORA can be fined up to one million Euros.
Additional penalties will be determined by each EU member state, and by the “competent authorities” and ESAs within them. These authorities may audit or suspend an entity or provider’s operations, send cease-and-desist orders and termination notices, issue public notices, or levy administrative or criminal penalties.
DORA and enterprise IT leaders
While IT leaders will remain key players in ICT risk management, DORA expands the capability beyond the domain of IT leadership in two ways:
- Most requirements for an organization’s ICT risk management will now be defined by external entities (European Supervisory Authorities, or ESAs)
- The internal management body for governing ICT risk management will now be cross-functional and include broader business leadership
How DORA will influence IT governance
DORA regulatory legislation mandates that financial entities establish or adjust their internal governance framework to align with its requirements. Financial entities must also establish or realign their management body. Non-technical board members, executive leaders, and other senior business managers are now expected to play an active role in IT governance, and can be held accountable if their entity fails to comply with DORA.
Who should care? Roles responsible for DORA
Maintaining compliance with DORA’s risk management framework will require a cross-functional effort. The following RACI chart outlines the various themes that must be addressed, and the teams and roles responsible for them.
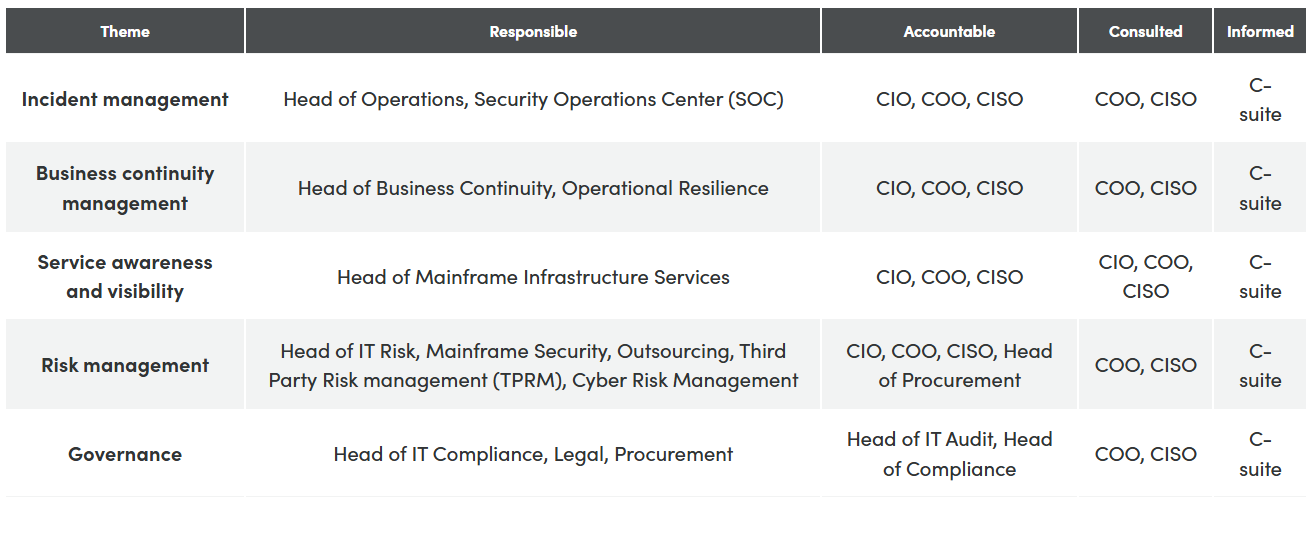
Major challenges: Operational resilience testing and incident reporting
Under DORA, banking entities and other financial entities must periodically test their operational resiliency plans. This includes testing to ensure they are prepared for likely disruptions, identifying and resolving deficiencies within their response plans. It also includes testing resilience against higher-level risks—such as ransomware attacks—through threat-led penetration testing (TLTP).
ICT-related incident reporting under DORA
In addition, DORA requires financial entities to expand their incident reporting capabilities and practices. DORA demands that entities:
- Establish systems for monitoring, logging, classifying, and describing incidents
- Report major ICT incidents (operational and security) to competent authorities
- Report significant incidents within 48 hours of discovery
- Send intermediate reports on incidents still in progress
- Report on root causes and remediation after an incident is resolved
- Communicate incidents to both DORA authorities and customers
- Voluntarily report significant threats they have discovered
- Follow all DORA guidelines, classifications, and templates for reporting
Third-party risks and resilience in the supply chain
Managing risk from third-party ICT providers is a core element of DORA. The legislation identifies significant risk from these providers and the supply chain as a whole. It defines requirements that third-party ICT providers must follow, as well as requirements for how financial entities must engage with their providers.
Both sets of requirements are detailed in greater length below.
ICT risk management framework: What DORA requires
The DORA act is an ICT risk management framework for financial entities. It seeks to expand ICT risk management beyond previous definitions, which primarily required entities to hold enough capital to mitigate their risks, and to unify these expanded risk management practices across all entities within the EU.
DORA also highlights “ICT risk management and governance” as one of its five pillars, and defines requirements that include, but are not limited to:
- Developing a ICT risk management framework
- Mapping all ICT systems
- Identifying and classifying critical assets
- Documenting ICT interconnections and dependencies
- Conducting continuous risk assessments of ICT systems
- Documenting and classifying cyberthreats
- Defining threat management protocols
- Conducting business impact analysis
- Establishing risk tolerance at multiple levels
- Implementing required cybersecurity capabilities
- Creating business continuity and disaster recovery plans
- Outlining communications and reporting plans in the case of a major ICT-related incident
- Testing of risk management and resilience practices
DORA also defines specific ICT risk management requirements related to third-party ICT providers, as well as new governance requirements. Both are detailed below.
Oversight framework: EU-level monitoring of third-party ICT providers
Third-party ICT providers that service financial entities—and are defined as “critical”—will be subject to an oversight framework imposed by DORA authorities, and will fall under direct supervision by EU financial authorities.
DORA authorities will monitor these providers to determine the risk that they bring to their customers, and to ensure they are managing their ICT risk properly. To do so, DORA authorities may request information and documentation on a provider’s risk management practices, perform investigations and inspections, recommend actions, and levy fines and penalties.
However, the DORA framework and the DORA authorities that manage it are not the only bodies responsible for third-party compliance with DORA. The legislation requires that individual financial entities reshape their relationships with these providers, as well, and take some accountability for managing their own supply chain risks.
Managing third-party risks: A crucial element of DORA
DORA regulatory legislation will become a standard element of all relationships between financial entities within the EU, and the third-party ICT providers that serve them.
The legislation seeks to increase the sector’s resilience against supply chain attacks and operational incidents, and to ensure financial entities can maintain continuity during these events. To do so, DORA places requirements on how entities understand and manage their third-party risks, and manage their relationships with providers.
Assessing the impact of third-party risks on operational resilience
- Financial entities will be required to map their dependencies on third-party ICT providers, and to document the vulnerabilities that each provider creates. Further, entities will be required to take active measures to mitigate the risks they uncover. These measures include, but are not limited to:
- Ensuring they are not too concentrated with any one provider or group
- Defining strategies for managing the risks their providers create
- Building fault-tolerant architecture in case a vendor experiences an incident
- Identifying exit strategies and substitutes for providers
Establishing guidelines for managing service providers
- Financial entities will take an active role ensuring their service providers meet DORA’s requirements. Entities will be expected to write DORA compliance into their contracts with providers. These clauses will ensure technical standards are met; exit strategies, audits, and resilience targets are defined; and risk is contractually managed.
- DORA authorities will support financial entities in these contract requirements. Financial entities will not be able to work with providers that are subject to DORA and do not meet its requirements, and authorities will be able to suspend or terminate contracts with providers that do not meet requirements, or fall out of compliance.
- In the future, DORA will likely include standardized contractual clauses and/or contract templates to streamline this process. Service providers will also likely make DORA compliance a standard feature of their service, like they have done with General Data Protection Regulation (GDPR) and other related regulations.
Developing relationships with ICT providers in a DORA context
- DORA compliance will become non-negotiable in every relationship between financial entities doing business within the EU and third-party ICT service providers.
- However, the degree of compliance and the terms that must be met will be subject to the same principle of proportionality as other elements of DORA. Financial entities will be expected to ensure a higher degree of compliance from third-party ICT providers that are more critical to their operations, and set a lower level of compliance for providers that are less critical to their operations and carry lower risk.
- By setting these requirements, DORA attempts to reduce the scale and impact of third-party provider risk within financial entities—and the sector as a whole—without becoming an unnecessarily high barrier to provider-entity relationships.
Assessing the impact of third-party risks on operational resilience
- Financial entities will be required to map their dependencies on third-party ICT providers, and to document the vulnerabilities that each provider creates. Further, entities will be required to take active measures to mitigate the risks they uncover. These measures include, but are not limited to:
- Ensuring they are not too concentrated with any one provider or group
- Defining strategies for managing the risks their providers create
- Building fault-tolerant architecture in case a vendor experiences an incident
- Identifying exit strategies and substitutes for providers
Establishing guidelines for managing service providers
- Financial entities will take an active role ensuring their service providers meet DORA’s requirements. Entities will be expected to write DORA compliance into their contracts with providers. These clauses will ensure technical standards are met; exit strategies, audits, and resilience targets are defined; and risk is contractually managed.
- DORA authorities will support financial entities in these contract requirements. Financial entities will not be able to work with providers that are subject to DORA and do not meet its requirements, and authorities will be able to suspend or terminate contracts with providers that do not meet requirements, or fall out of compliance.
- In the future, DORA will likely include standardized contractual clauses and/or contract templates to streamline this process. Service providers will also likely make DORA compliance a standard feature of their service, like they have done with General Data Protection Regulation (GDPR) and other related regulations.
Developing relationships with ICT providers in a DORA context
- DORA compliance will become non-negotiable in every relationship between financial entities doing business within the EU and third-party ICT service providers.
- However, the degree of compliance and the terms that must be met will be subject to the same principle of proportionality as other elements of DORA. Financial entities will be expected to ensure a higher degree of compliance from third-party ICT providers that are more critical to their operations, and set a lower level of compliance for providers that are less critical to their operations and carry lower risk.
- By setting these requirements, DORA attempts to reduce the scale and impact of third-party provider risk within financial entities—and the sector as a whole—without becoming an unnecessarily high barrier to provider-entity relationships.
DORA compliance: A strategic checklist for IT leaders
DORA is a complicated set of regulations with an extensive list of new requirements and technical standards to meet. Bringing it to life will be difficult for many financial entities and third-party ICT providers. The following checklist provides a simple way to get started building compliance as quickly as possible.
Assessing current ICT systems and identifying gaps
Some of DORA’s requirements are easy to assess against, others are not. For example, DORA specifically states that a financial entity’s backup data must be logically and physically segregated, and that it must be able to test its recovery plans once per year. These are concrete requirements that you either meet or need to develop.
Other DORA requirements are more ambiguous. For example, DORA states that cyberattacks need to be “promptly and quickly” resolved. While DORA states that critical functions must be recovered within two hours of the incident, there is no clear-cut timeline for when an incident must be resolved in full.
Creating a culture of cyber resilience in financial institutions
Every requirement in the DORA regulation focuses on building cyber resilience—the ability to withstand and recover from any disruptive incident. Resilience goes beyond simply developing business continuity plans and disaster recovery protocols, and creates additional systems to deal with complex, modern threats like ransomware attacks.
A culture of resilience focuses on five core competencies:
- Identifying risks outside of known attack patterns
- Protecting critical data and systems to limit the likelihood and impact of an incident
- Detecting problems ASAP
- Responding to events with well-defined mechanisms
- And recovering data and operations efficiently and effectively
Essential collaboration between IT teams and regulatory bodies
In the past, financial entities and EU member states all followed their own protocols and standards. This created a patchwork of regulations and best practices that opened vulnerabilities and made compliance difficult to navigate. DORA seeks to standardize protocols to create a unified, secure EU financial sector.
This is a collaborative effort. The DORA law requests feedback from entities, voluntary sharing of threats, and open reporting of incidents. Maintaining open dialogue with DORA’s authorities not only makes the framework more effective, but it also keeps entities in the loop on ever-changing regulations so they can stay ahead of new requirements.
Meeting new technical standards
A financial entity’s ability to meet DORA’s technical standards largely depends on its tools and partnerships with compliant, experienced providers. The first step will be leveraging pre-existing structures, capabilities, and relationships that need to be tweaked or expanded to fill gaps in DORA’s requirements.
However, most entities will need to make additional investments. For example, while many financial entities already have a second backup data storage system in place, DORA states they must have immutable backups that are physically and logically segregated from all other sources, which typically requires investment in a third, cybervault technology.
The future of financial operational resilience
DORA does not exist in a vacuum. It follows and closely mirrors other regulations that attempt to standardize and improve cybersecurity practices across the EU, and it will likely inform a large number of coming regulations in multiple industries.
Predicting the evolution and impact of DORA
DORA will improve cybersecurity and outline operational resilience regulations for financial entities as well as entities in many other industries. The reason for this is twofold. First, DORA sets higher standards for third-party ICT providers. Few of these providers only service the financial sector. Most of them serve organizations in every industry. By forcing third-party ICT providers to increase their security and resilience, DORA will reduce their risk for everyone who works with them—not just financial entities.
Second, DORA will likely inform broader regulations that apply to all industries, and are passed by countries outside of the EU. Financial services—and the EU—have long set the standard for cyber regulations. Just like GDPR’s requirements have become the global standard for data privacy, it is likely that the DORA requirements will be adopted by many other frameworks.
The act itself will continue to evolve, and financial entities and the providers that serve them should expect DORA updates that will further standardize practices and requirements for cybersecurity and digital resilience. The future is more regulations around these topics, not less, and IT leaders would do well to stay ahead of the curve.
The role of enterprise IT leaders in fostering a culture of resilience
DORA may be a cross-functional framework that makes cyber resilience a board-level concern, but it still lives primarily within the IT domain. IT leaders in operations, security, and risk will have the primary responsibility for meeting its requirements, as they “own” the digital systems that DORA is concerned with protecting.
This responsibility will only increase as more and more financial systems become digitized and dependent on ICT systems, whether internal or from third-party providers. DORA makes it clear that IT leaders are the present and the future of maintaining resilient operations within financial entities.
How should I prepare for DORA? What to focus on today.
The sooner you start, the better.
The DORA law goes into effect on January 17, 2025, and many of its requirements will take time to put into place. Focus on the biggest gaps within your compliance that will require the most investment and effort to implement.
For most financial entities, that will be:
- Implementing a third, immutable backup of data that is physically and logically segregated from primary and secondary sources
- Creating systems to recover data within two hours of an incident
- Developing the ability to manually test those systems at least once per year
BMC provides solutions and ICT services to rapidly bring these capabilities to life, in addition to a full portfolio of tools to cover every other element of operational resilience.
To learn more and request assistance in understanding DORA and achieving compliance by January 2025, reach out today for a consultation.
Resources
- Webinar: Operational Resilience for the Mainframe: A DORA Survival Guide
- Futurum Group Brief: DORA Compliance and Resiliency for the Mainframe: Proactive Strategies for Operational Continuity
- E-book: The DORA survival guide for mainframe operational resilience
- Infographic: The clock is ticking on DORA. Is your mainframe ready?
- Podcast: Mainframe Operational Resilience - DORA and Beyond
- Blog: Mainframe Blog Navigating DORA Regulations: A Guide for Mainframe Operational Resilience
- Intellyx White Paper: Mainframe Observability: More than Monitoring
- Blog: What DORA Means for Mainframe Teams in and Around EMEA
- White Paper: Make DORA your friend to boost both security and mainframe budget
- White Paper: Mainframe Under Attack: Essential Measures for Ransomware Resilience